Secure Access is Oplon Networks' answer to replace dangerous VPNs, guarantee secure access to Web services, Linux / UNIX and Windows machines and thus prevent the intrusion and spread of viruses in data centers and corporate networks. Secure Access can be used from any device and without installing any client, just use any web browser to have access to all the services available.
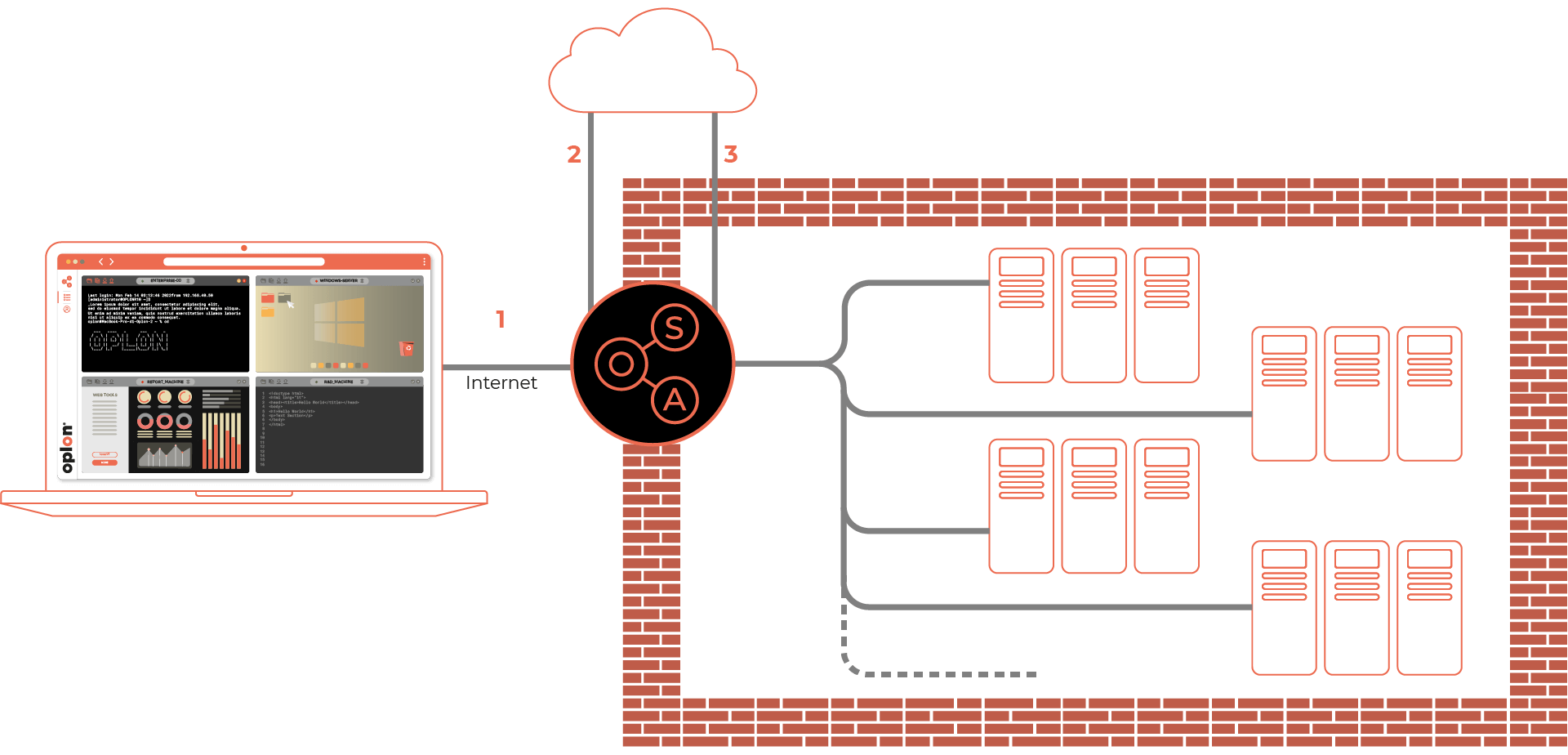
OSA architecture is simple, it aims to guarantee safety and privacy to your data while fully respecting every GDPR policy.
Moreover, the solution is built to counteract the most modern cyber-attack, which often resorts to AI in order to violate Cloud systems, putting at risk the confidentiality of your information. The virtual appliance OSA lives inside your perimeter, making no difference if it’s in-cloud, on-premises or hybrid-cloud based. It will grant you full ownership over your data without the risk of it being disclosed externally. With Oplon Secure Access, safety is granted by using just and only the browser, it doesn’t require neither the use of VPNs, nor the installation of plugins or extensions, letting you forget exhaustingly endless calls with the help desk for connection problems. From today, thanks to OSA, you can connect to datacenters in simplicity while maintaining the highest level of protection.
Oplon Secure Access stands out for its excellence in ensuring compliance with key data security and protection regulations, such as GDPR, NIST and NIS2.
It ensures the protection of personal data, adopts best security practices and effectively manages risks, safeguarding critical infrastructures and ensuring business continuity.
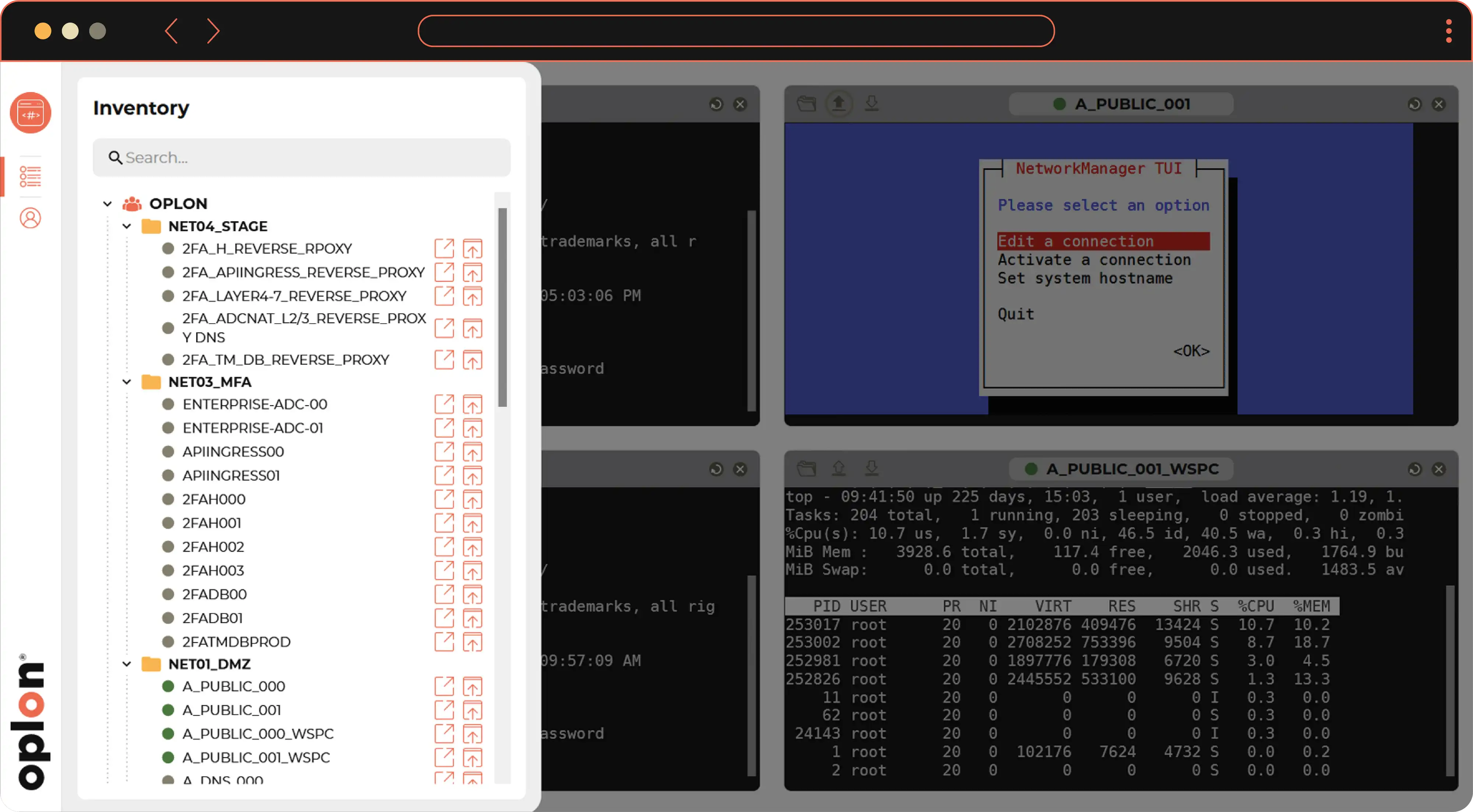
The operator will have access to a set of resources predetermined by a figure called Manger. These resources can be grouped in logical contexts such as the network topology, or they can be grouped by service areas such as e-commerce, restricted areas. This allows you to authorize the user with a specific profile, from the beginning, exclusively to a set of applications of his competence, applying the criteria of the Zero Trust Architecture and to revoke it when they are no longer needed, avoiding leaving "doors open". It also facilitates the understanding of the infrastructure, simplifies its maintenance as much as possible and avoids authorization errors.
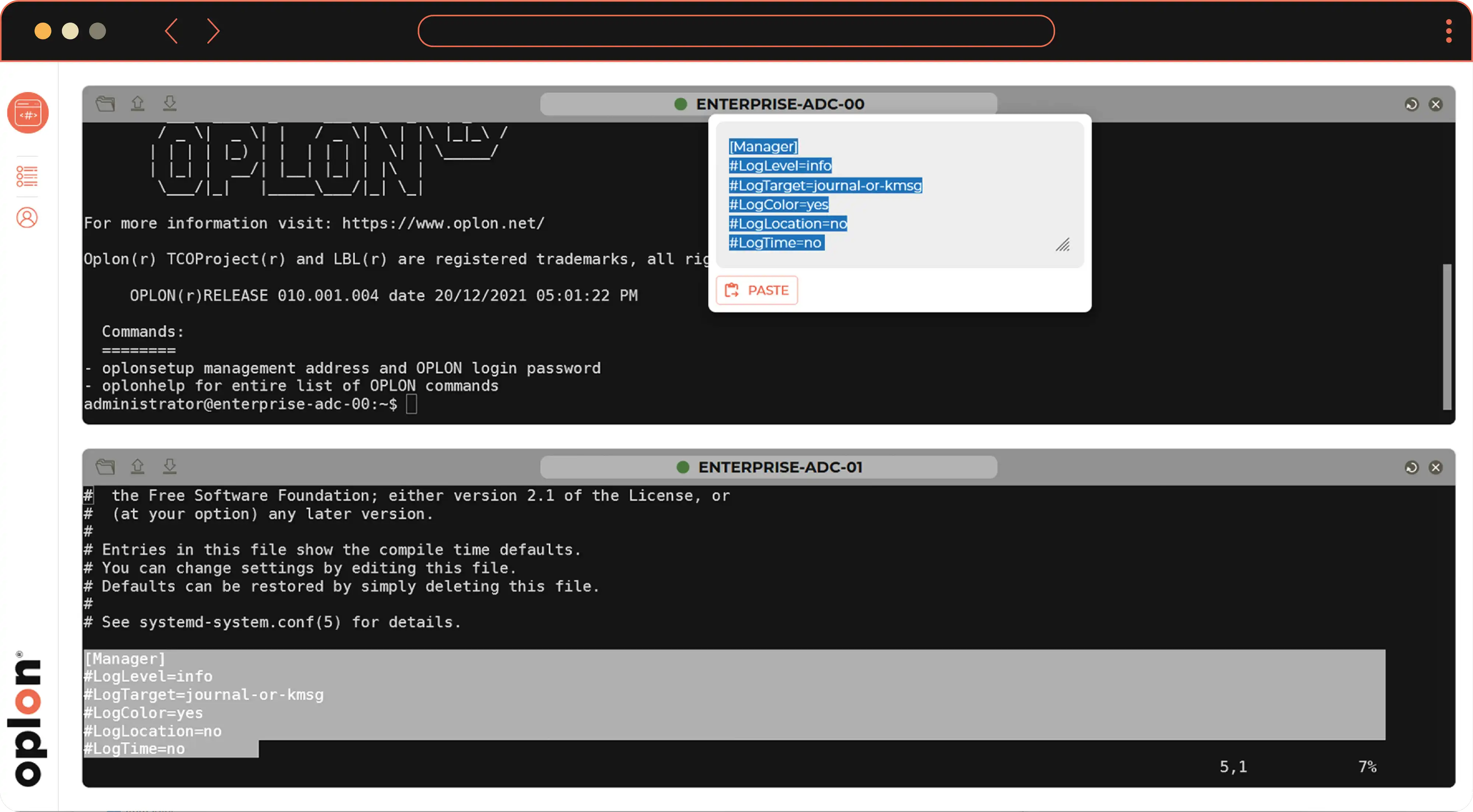
The 'copy' and 'paste' function has been carefully studied to guarantee the same experience of the tools normally used up till now. For the copy operations it is sufficient to select the desired text, while the paste is activated with right click (or from the keyboard using CTRL + Shift + V). All this takes place without enabling the clipboard reading, giving Secure Access maximum security.
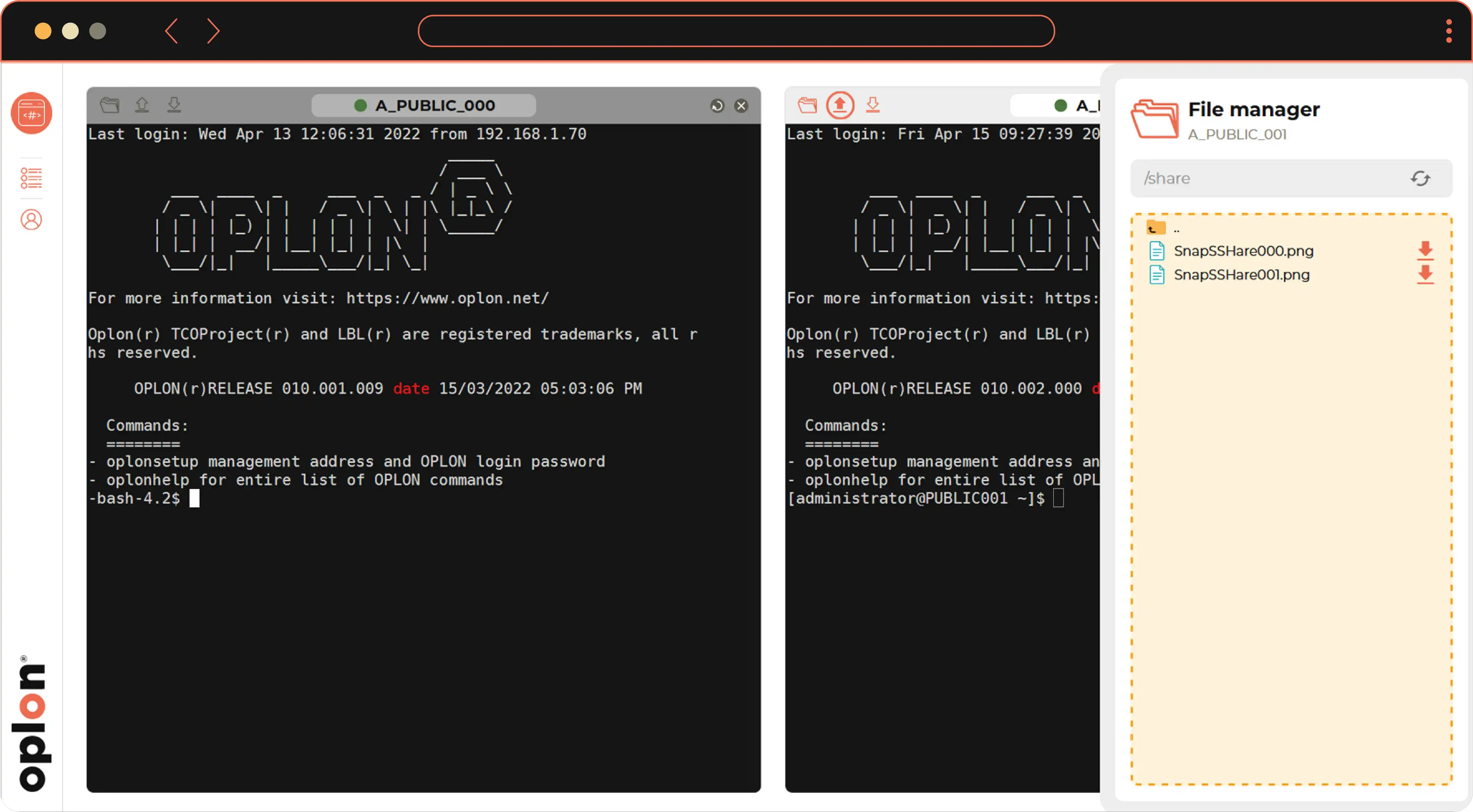
Upload and Download have been made simple and contextual. Just select the File Manager icon of the relevant session to open a menu that will allow you to browse the file system, upload files with a simple 'Drag and Drop' and download files remotely, locally. Simplicity and security, all transfers and all operations are tracked on the centralized database available to Managers.
The layout of the work sessions on the web browser is aided by the Layout Manager which allows you to tile the windows. The operator is able to increase his productivity by organizing the workspace as he sees fit and switching from one context to another with a click, with the facilitation of zooming and resizing added to applications for which they are not natively available. Oplon Secure Access provides the same usability that the browser also makes available for Windows / Linux interfaces. To increase the characters just press CTRL + and to decrease them CTRL –
Oplon Secure Access include una piattaforma MFA ad alta sicurezza, l’utente è identificato in maniera sicura con un secondo fattore di autenticazione a scelta tra App per smartphone (Apple/Android) con riconoscimento biometrico, la più sicura oggi esistente sul mercato, oppure tramite email.

No VPN that connects the operator directly to the data center. With Oplon Secure Access, security is guaranteed by default by using the browser.
With Oplon Secure Access, the only client you need to use is your favorite. The operator will not have to install anything, making the help desk operations less expensive.
Login and password must no longer be disclosed to administrators and end users. Oplon Secure Access takes care of access, both in protected internal WEB services, Remote Desktop and Consoles with remote shell, in a centralized and authenticated manner for any user. The credentials remain protected, access can also be timed, or assigned and revoked by the administrator.
Oplon Secure Access performs a total and unmodifiable tracking of operations performed by the user, including file upload/download operations. This allows, for example, to be complaint with the GDPR regulations regarding root or administrative access of Linux/Unix devices.
For the external connection, operators often use third party products that do not provide any guarantees, often saving the credentials. With Oplon Secure Access it is enough to simply use the browser and only remember the access password, that is that of the multi-factor authentication. The credentials safe remains secure and not accessible within the company system.